Cross-Site Request Forgery (CSRF) is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the web application trusts. It is classified as a server-side vulnerability and targets state-changing requests, not data theft (as is the case with cross-site scripting).
CSRF exploits the trust that a web application has in a user’s browser by leveraging stored credentials such as cookies. Unlike XSS, which exploits the trust a user has in a website, CSRF exploits the trust the website has in the user.
Concept and Mechanism
When a user is authenticated in a web application, a session is established. The server identifies the session through a session ID, typically stored in a cookie. If an attacker can induce a logged-in user to submit a forged request, the server will process it using the user’s authenticated session.
A common example is a banking application that allows users to transfer funds using a URL like:
https://bank.example.com/transfer?to=12345&amount=1000
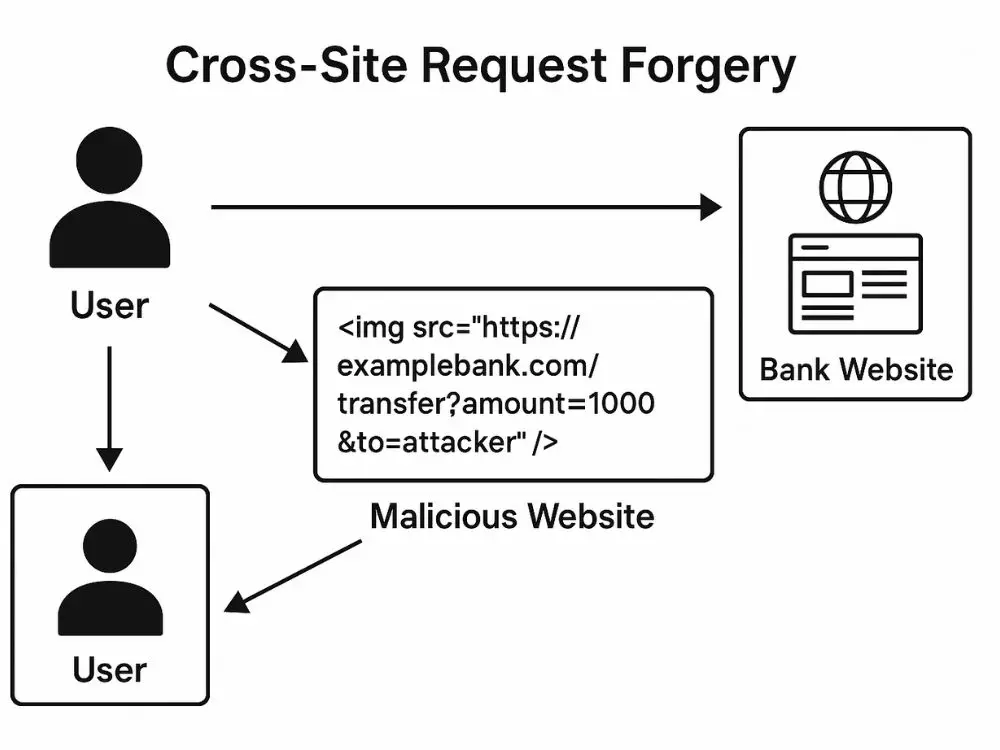
If the application does not implement CSRF protection, and a logged-in user visits a malicious site that includes:
<img src="https://bank.example.com/transfer?to=attacker&amount=1000" />
The browser will send the request along with the authentication cookie, completing the transfer without the user’s knowledge.
Characteristics
- Authentication context: CSRF requires the user to be authenticated.
- Blind exploitation: The attacker cannot see the result of the request but relies on predictable behavior.
- Common vectors:
GETandPOSTrequests embedded in HTML forms or tags such as<img>,<script>, and<iframe>.
Prevention Techniques
Several well-established mitigation strategies are available to reduce or eliminate the risk of CSRF:
Anti-CSRF Tokens
A CSRF token is a unique, secret, and unpredictable value that is generated by the server and included in each HTTP request made by the client. The token is validated on the server side to confirm the legitimacy of the request.
Example in HTML form:
<form method="POST" action="/update-email">
<input type="hidden" name="csrf_token" value="a9f8sdf8as98dfas9" />
<input type="email" name="email" />
<input type="submit" value="Update Email" />
</form>
If the token is missing or invalid, the server should reject the request.
SameSite Cookie Attribute
The SameSite attribute of HTTP cookies allows developers to declare if their cookie should be restricted to a first-party or same-site context.
Set-Cookie: sessionid=abc123; SameSite=Strict; Secure
Strict: Prevents the browser from sending the cookie along with cross-site requests.Lax: Permits sending cookies with top-level navigation GET requests.None: Cookies will be sent in all contexts, but must be marked asSecure.
Referer and Origin Header Validation
The server may check the Referer or Origin HTTP headers to verify that requests originate from a trusted domain. While not foolproof, this is an additional validation layer.
Example (in Node.js):
if (req.headers.origin !== 'https://yourdomain.com') {
res.status(403).send('Forbidden');
}
Reauthentication for Sensitive Actions
Some applications enforce reauthentication before executing critical operations, such as password changes or large fund transfers. This minimizes the risk of a CSRF exploit by requiring user interaction.
CSRF in Modern Web Frameworks
Most web frameworks provide built-in protection mechanisms against CSRF:
- Django: Uses middleware to inject and validate CSRF tokens.
- Ruby on Rails: Provides CSRF protection by default.
- Laravel: Automatically generates and verifies CSRF tokens.
- Express.js (Node.js): Middleware such as
csurfcan be used to enable token validation.
CSRF vs XSS
| Feature | CSRF | XSS |
|---|---|---|
| Target | Web application trusting the user | User trusting the web application |
| Requires Login | Yes | No |
| Vector | Malicious form or link sent to the user | Malicious JavaScript injected into the website |
| Outcome | Unauthorized state change | Information theft or malicious content execution |
Specification and Industry References
CSRF is covered in detail in the OWASP Top Ten, under category A05:2021 – Security Misconfiguration or previously under A08:2017 – Insecure Deserialization, depending on how the token is generated or stored. Additionally, most modern web browsers support cookie protection using the SameSite attribute, as defined in RFC 6265bis.
For security-conscious developers, incorporating CSRF protection is essential in any application that relies on session-based authentication and processes user input.
Summary
Cross-Site Request Forgery is a critical web security vulnerability that targets authenticated sessions. It forces users to perform unintended actions without their consent. The use of anti-CSRF tokens, secure cookie attributes, and request validation techniques significantly reduces the attack surface.
CSRF prevention should be considered a fundamental part of secure application design.
JavaScript: Which of the Following is Not a Valid Way to Define a Variable?
browser rendering optimization